Connecting to PlanetScale for Postgres privately via AWS PrivateLink
AWS PrivateLink is a highly available, scalable technology that enables you to privately connect your VPC to supported AWS services, VPC endpoint services, and AWS Marketplace partner services. When you use AWS PrivateLink, your network traffic between your VPC and PlanetScale stays within the AWS network, without traversing the public internet.When to use AWS PrivateLink
By default, PlanetScale for Postgres databases use secure connections over the public internet with industry-standard TLS encryption. This approach is secure and meets the needs of most customers. However, you may want to consider AWS PrivateLink if:- Compliance requirements: Your organization has stronger regulatory or compliance mandates that require database connections to avoid the public internet entirely
- Enhanced security posture: You want an additional layer of network isolation for sensitive data workloads
- Network architecture: Your existing AWS infrastructure is designed around private connectivity patterns
- Reduced network latency: AWS PrivateLink can help reduce latency by avoiding the extra network hop through a NAT gateway that’s typically required for outbound internet connections from private subnets. While this latency difference is often minimal (typically single-digit milliseconds), it may be noticeable if you’re migrating from a database that was previously hosted directly within your VPC
Normal PlanetScale for Postgres connectivity (as described in our standard connection documentation) uses secure TLS encryption over the public internet and is appropriate for most use cases. AWS PrivateLink is primarily beneficial for compliance and enhanced security requirements.
PrivateLink pricing
PlanetScale does not charge any additional fees for AWS PrivateLink connectivity. However, AWS charges standard PrivateLink pricing for VPC endpoints, which includes:| Charge Type | Rate | Description |
|---|---|---|
| VPC endpoint hourly charges | ~$0.01 per hour | Per VPC endpoint (varies by region) |
| Data processing charges | ~$0.01 per GB | Data processed through the VPC endpoint (varies by region) |
Prerequisites
- A PlanetScale for Postgres database in an AWS region
- An AWS VPC in the same region where you want to establish the private connection
- Appropriate AWS IAM permissions to create VPC endpoints (see AWS VPC endpoint permissions documentation)
- Appropriate AWS IAM permissions to create and modify Security Groups (see AWS IAM permissions for security groups documentation)
Establishing a VPC endpoint
- Retrieve the Private Service Name:
- From the PlanetScale organization dashboard, select the desired database
- Navigate to Settings from the menu on the left
- Select Roles
- Click on a role with permissions to the relevant
Branch - Copy the
Private HostandPrivate Service Namefrom the role details
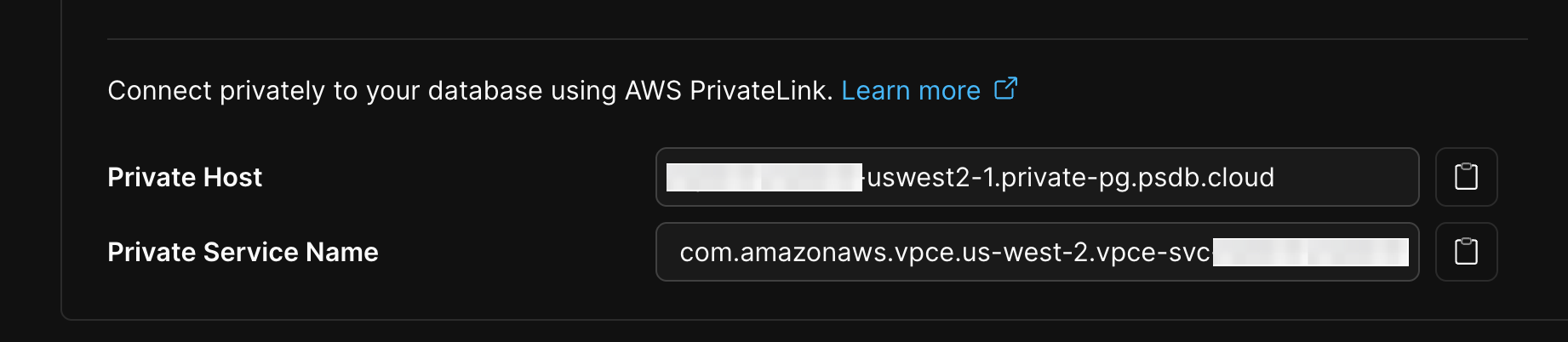
Both the
Private Host and Private Service Name values are the same for all roles for a given PlanetScale database Branch. Once enabled, any role can use the PrivateLink endpoint. You do not need to configure this per PlanetScale Role.-
Create a Security Group for the Endpoint:
You will need an AWS Security Group configured to allow inbound traffic for the required ports. You can configure access using either the security group ID of your application hosts, your VPC’s CIDR configuration, or specific subnet CIDR configurations. Ensure your security groups allow:
- Inbound PostgreSQL (port 5432): For direct database connections
- Inbound PSBouncer (port 6432): For pooled connections via PSBouncer
Replace<your-vpc-id>with your actual VPC ID. You can find your VPC ID and its CIDR block using: -
Navigate to VPC Endpoints: In your AWS Console:
- Confirm you are in the proper
<aws-region>from the dropdown on the top right - In the search field at the top left enter “Endpoints”.
- Click the link listed as a VPC Feature.

- Confirm you are in the proper
-
Create a new endpoint: Click “Create Endpoint”.

-
Select endpoint type: Choose “Endpoint services that use NLBs and GWLBs”.

-
Enter service name: Enter in the “Service name” text box the
Private Service Nameretrieved from the PlanetScale dashboard. Click “Verify service” to confirm the service exists.
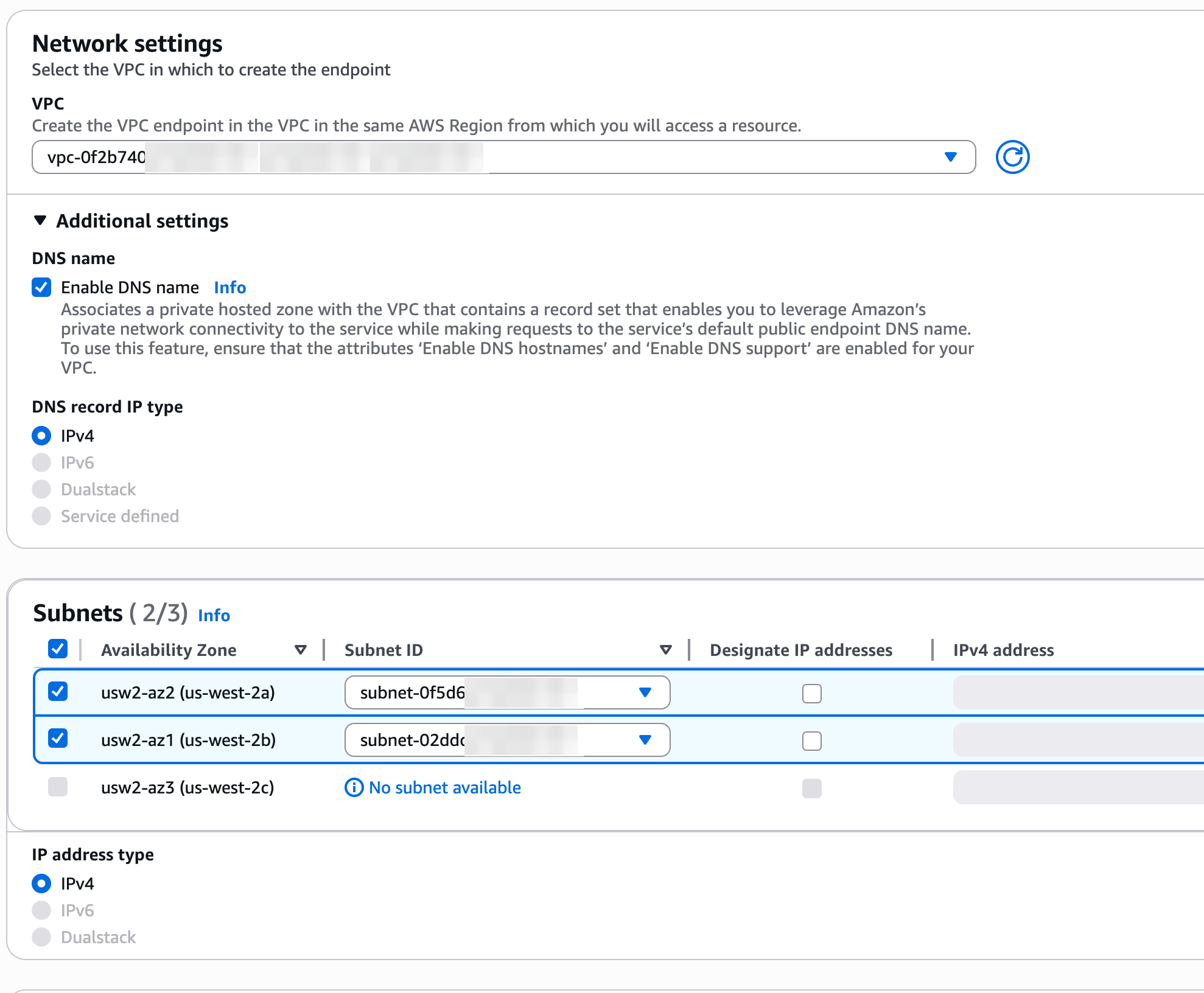
- Configure VPCs: Choose the VPC that should have access to the PlanetScale service endpoint.
- Enable DNS names: Click the “Additional settings” dropdown arrow to reveal DNS configuration options, and select the “Enable DNS name” checkbox.
- Configure Subnets: Choose the subnets that should have endpoint interfaces for the PlanetScale service endpoint. It is recommended that you select at least 2. You should select subnets that your application servers have access to.
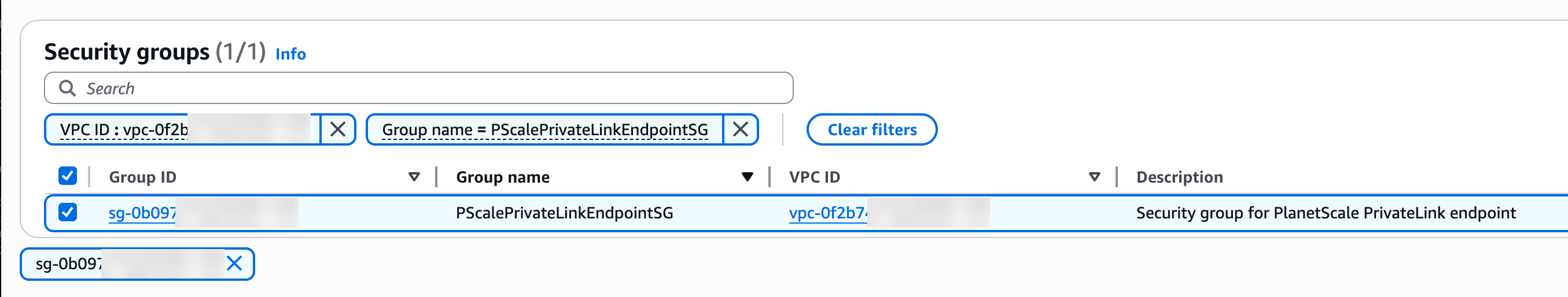
- Configure security groups: Choose the appropriate security group to control which resources can send traffic to the PlanetScale service endpoint. Use the one created earlier if you created one for this purpose.
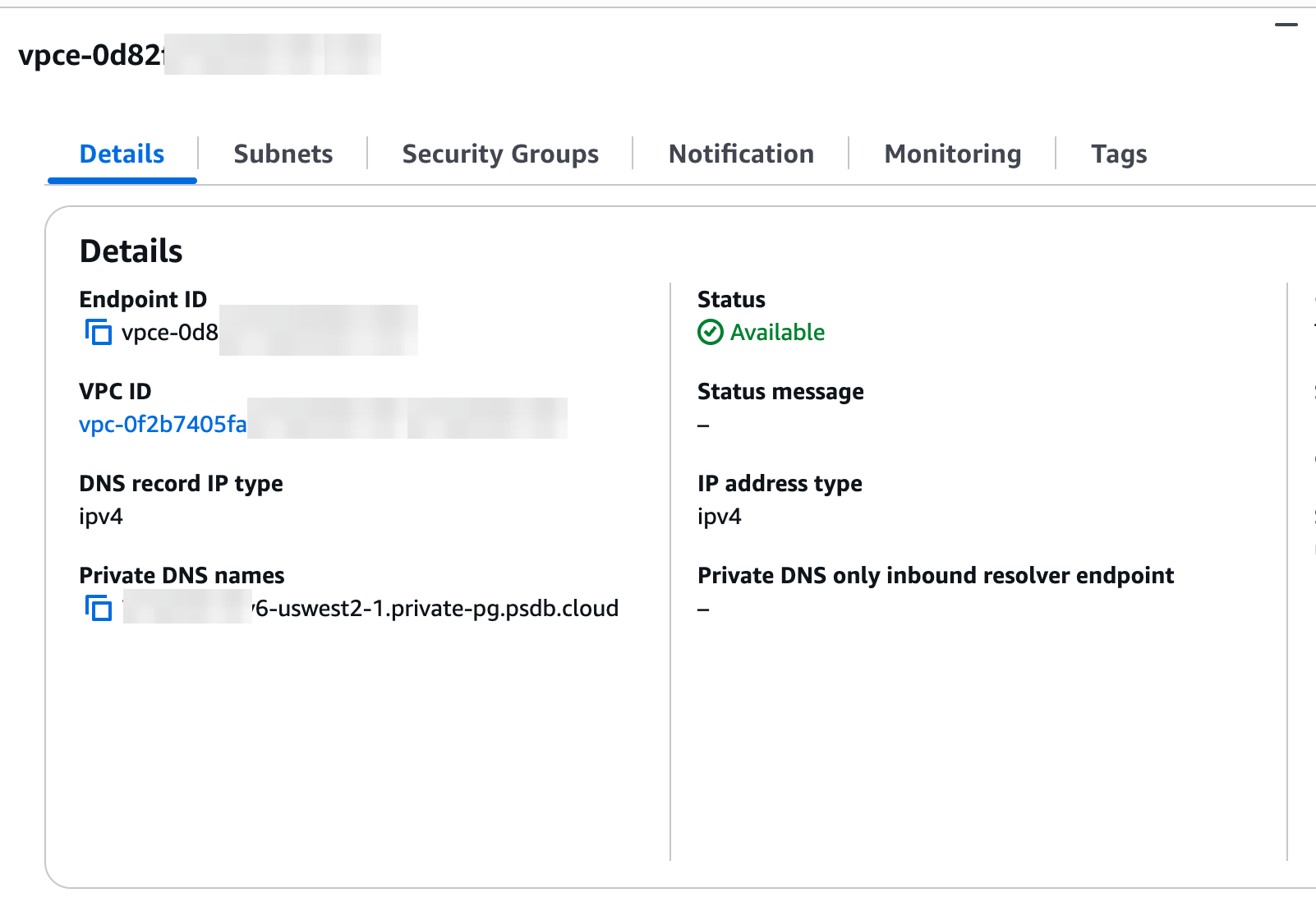
- Create the endpoint: Click “Create endpoint” and wait for the VPC endpoint status to show “Available” (this may take several minutes).
Verifying your VPC endpoint connectivity
- Confirm endpoint status: In the AWS Console, verify that your endpoint’s status shows “Available”.
-
Test DNS resolution: From an EC2 instance in your configured VPC, run a DNS lookup to confirm resolution to your VPC’s IP range. Use the
Private Hostyou recorded earlier from the PlanetScale dashboard: -
Test your new connection:
Once you have confirmed DNS resolution, test the private endpoint:
Update your connection strings
Once your VPC endpoint is established and verified, you’re ready to update your application’s connection strings to use the private endpoint address instead of the standard public endpoint.Security group considerations
Ensure your security groups allow:- Outbound PostgreSQL (port 5432): For direct database connections
- Outbound PSBouncer (port 6432): For pooled connections via PSBouncer
- Inbound - any application-specific ports: Based on your connection requirements
Network ACL considerations
VPC Network ACLs (NACLs) operate at the subnet level and provide an additional layer of security beyond security groups. For AWS PrivateLink connections to PlanetScale, ensure your NACLs allow:- Outbound PostgreSQL (ports 5432, 6432): For database connections
- Ephemeral ports (1024-65535): For return traffic from AWS PrivateLink endpoints
Troubleshooting
If you’re experiencing connectivity issues:- Verify endpoint status: Ensure your VPC endpoint shows “Available” status
- Check security groups: Confirm your security groups allow the required ports
- Check NACLs: Confirm that your VPC’s NACLs are configured to allow the correct network traffic
- Test DNS resolution: Verify DNS is resolving to private IP addresses in your VPC CIDR range
- Use AWS Reachability Analyzer: The Reachability Analyzer allows you to inspect the path between two resources (such as a client and your PlanetScale for Postgres endpoint) and provides guidance on why connectivity might be failing
- Contact support: If issues persist, contact PlanetScale support with your endpoint configuration details
Next steps
- Learn about PostgreSQL roles and permissions
- Configure connection pooling with PSBouncer
- Monitor your connections and performance

